
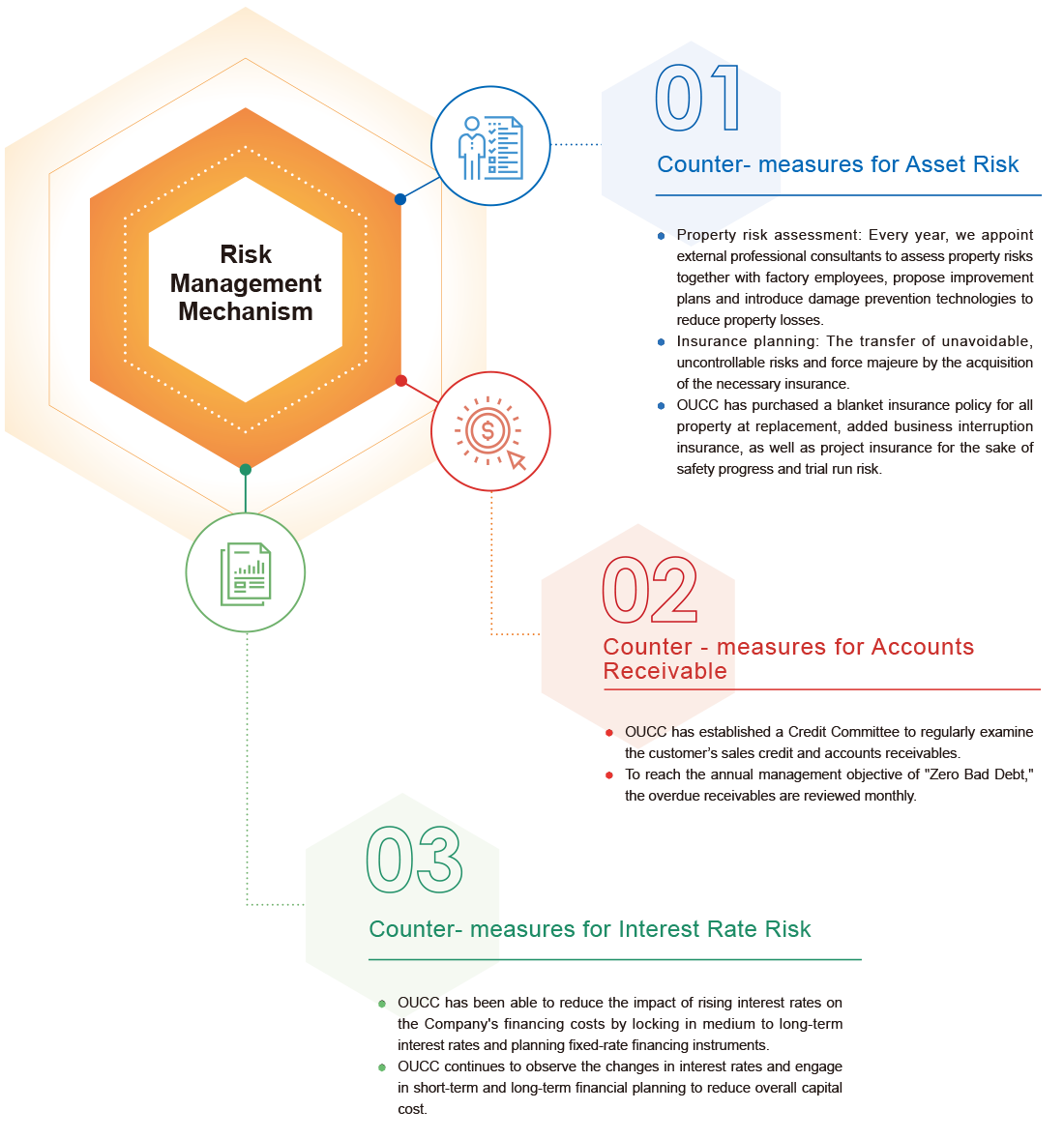
Risk Management
OUCC places great emphasis on risk management. In addition to the daily information security, defense of hacker attack, the company has incorporated the geopolitical risks and had removed all the data to the cloud data center as a countermeasure.
For critical operational issues and risks, we conduct systematic evaluations and analyses. We implement relevant management systems, develop well-defined risk strategies and actions, and integrate them with sound operational management practices. This ensures the balance between business operations and risks, establishing a solid foundation for sustainable business practices.
Task Force on -
Climate related Financial Disclosures (TCFD)
To transparently disclose climate change-related risks and opportunities, and to ensure that stakeholders understand OUCC's efforts and strategies in addressing climate change.
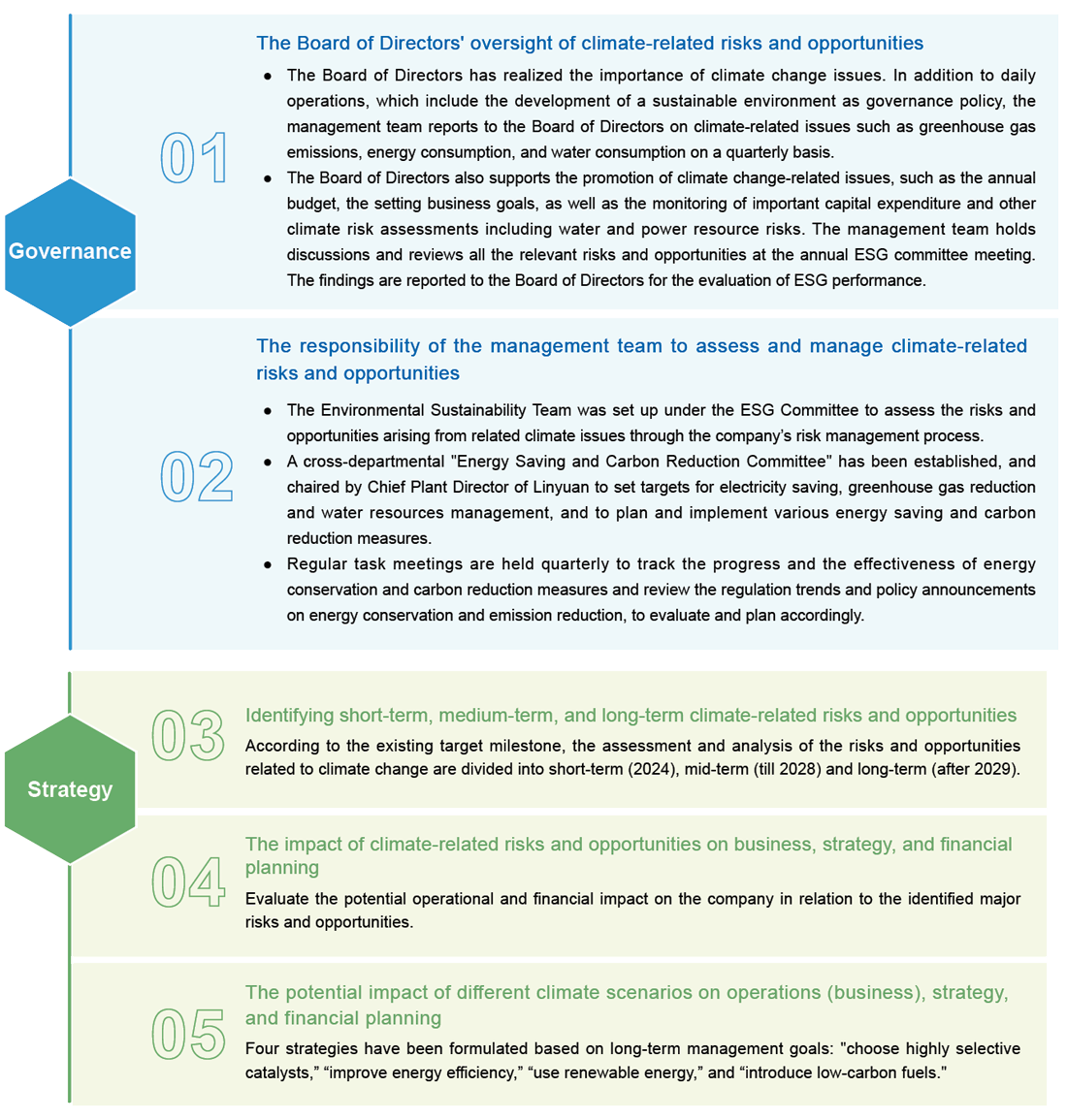
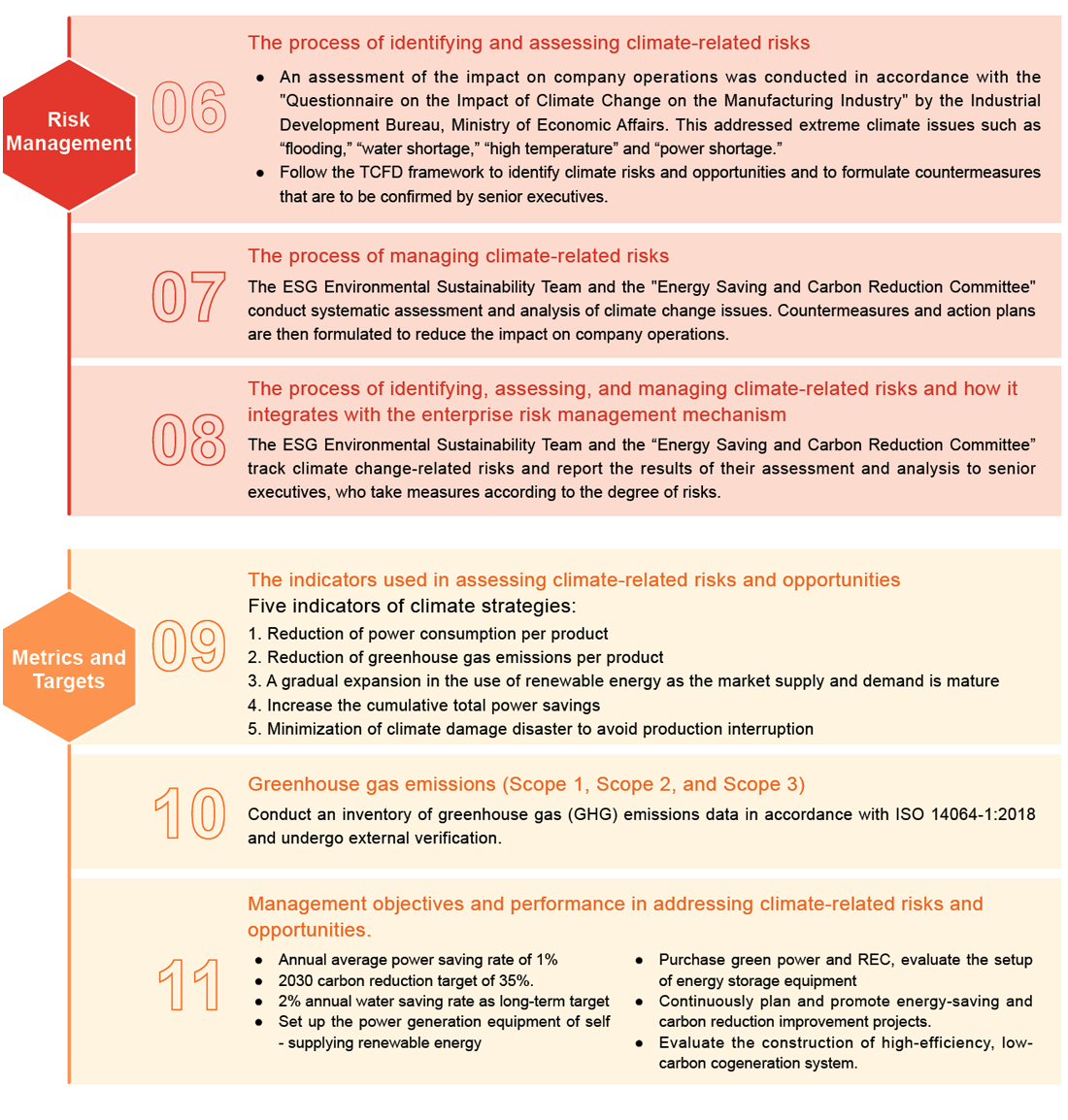
OUCC adopted the "Recommendations of the Task Force on Climate-Related Financial Disclosure (TCFD)" framework in 2023 to measure and evaluate the impact of climate change through the four major frameworks of governance,
strategy, risk management, and metrics and targets, evaluate and disclose the potential business impact of climate change issues on OUCC, and develop countermeasures to reduce the potential impact of climate change risks on our operations.
Task Force on Climate-related Financial Disclosures (TCFD) comparison table
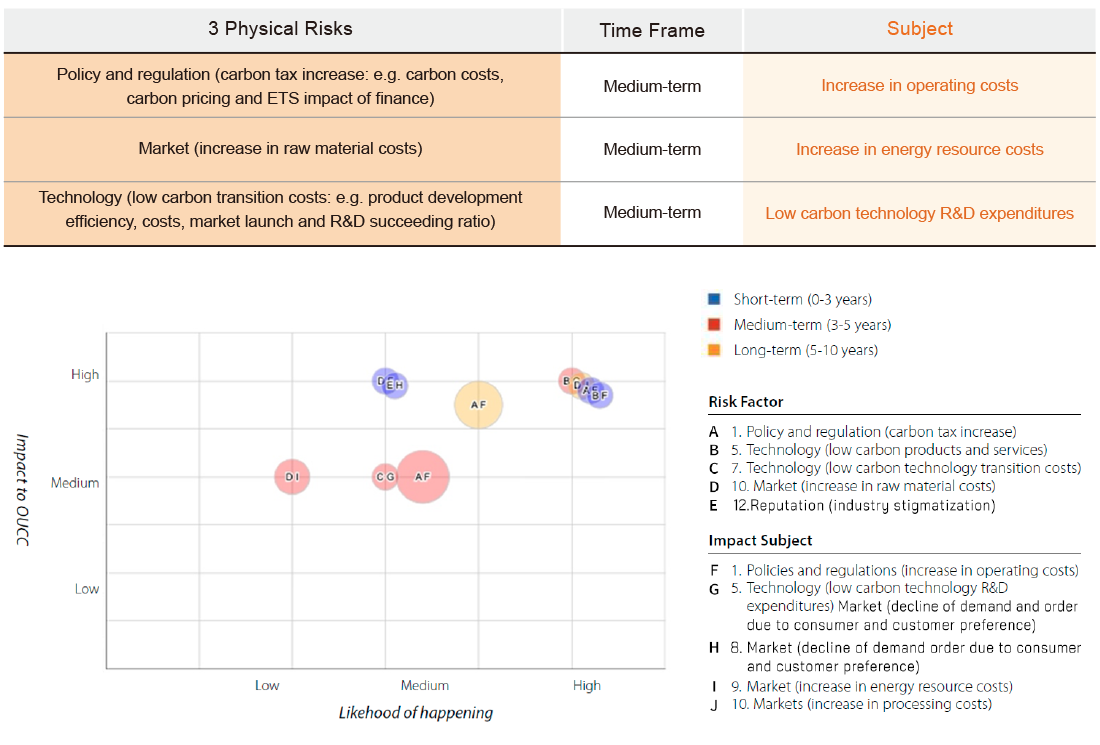
OUCC Material Climate Risk Matrix
Physical Risks Matrix

Trasitional Risk Matrix
Business Integrity
To implement the integrate management and eliminate improper business practices, the OUCC has formulated the "Best Practice Principles of Ethical Corporate Management" and "Code of Ethics" and provided regular education and publicity to regulate the business conduct of Directors, Managers, and employees. In 2023, 396 employees participated in 354 hours of training.
We require Directors and senior management to issue a statement of compliance with the integrity management policy. It stipulates that Directors, Managers, and employees shall not directly or indirectly provide, promise, request, or accept any improper benefits, engage in dishonest acts that violate integrity, or breach fiduciary obligations while engaging in business conduct.
The preceding policies and provisions are published on the company website to communicate and publicize to relevant stakeholders. OUCC shall issue punitive actions for any violation of the preceding provisions according to law. We also provide multiple communication channels. If there is a violation of the integrity management regulations, the illegal behavior can be reported through the appropriate channels, which will be handled confidentially.

Sound Internal Control System
Designed by the managers and approved by the Board of Directors, the internal control system of the OUCC is to be implemented by the Board, the management, and other employees and is designed to provide sound management and to achieve objectives of the internal control system.

Internal Audit
Effective operation of the internal control system is ensured by an independent audit department which is subordinate to the Board of Directors. In addition to regular business audit reports to the Audit Committee, the audit officer also reports at the Board of Directors meetings.
OUCC places high value on ESG related issues, internal control, and the internal audit. The 2023 audit plan included reviews on corporate governance, financial operations, environmental and labor safety, as well as information, R&D and other related operations, which were conducted to ensure the company operations and information disclosure met with the expectations of all the stakeholders.

Information Security Risk Management
To safeguard the information from the impact of unendurable risks, OUCC adopts the cloud data center offer from AWS, through migrating databases of the company to the cloud data center of Amazon Web Services (AWS), which service indicator topped 99.99999999, ensuring the sustainable operation of the company and the security of customer information.
1.IT Security Organization
For the "IT Security Management Organization," OUCC has set up an IT security manager as an information security management representative to supervise information security, and a IT personnel accountable for IT policy implementation.

2.Management Approach
OUCC’s risk transfer and contingency strategies include management mechanisms such as risk assessment, risk transfer, emergency response and maintenance audit to secure proper operation of the information system.

3.Action Plans
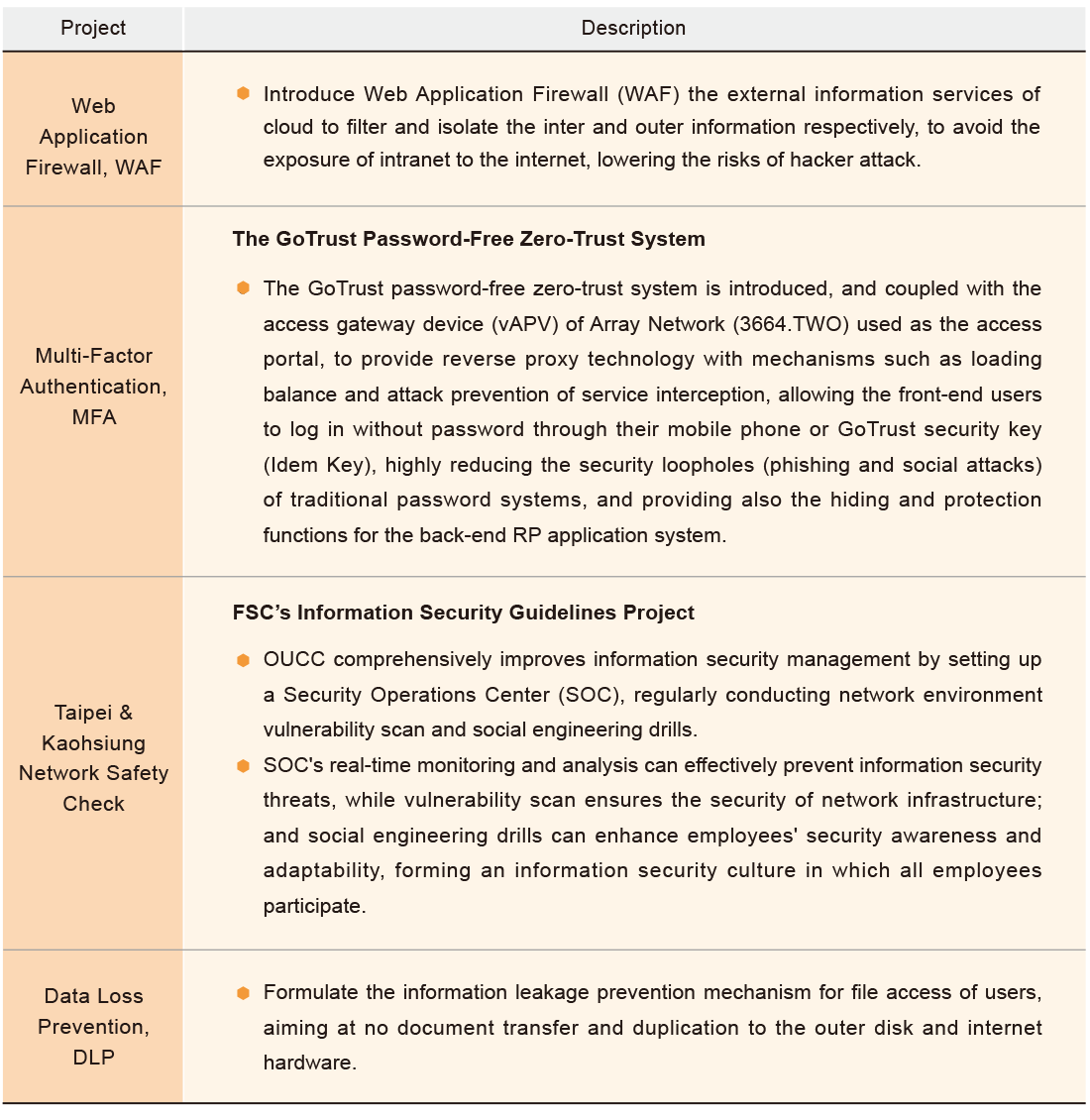
In 2023, we implemented the two-tier authentication mechanism for personnel external login for business purposes, and introduced the GoTrust password-free zero-trust system coupled with the access gateway device (vAPV) of Array Network (3664.TWO) used as the access portal, to provide reverse proxy technology with mechanisms such as loading balance and attack prevention of service interception, allowing the front-end users to log in without password through their mobile phone or GoTrust security key (Idem Key), highly reducing the security loopholes (phishing and social attacks) of traditional password systems, and providing also the hiding and protection functions for the back-end RP application system. For relevant business information security, we also introduced SSL certificates to establish a standard specification for a password link between the website server (host) and the website browser (client), so that clients’ and internal information can be secured and without being monitored.

The following measures are adopted to manage the employees’ privately owned computers at workplace:
- Controlling devices' unauthorized access to the company intranet (802.1X)
- Setting different policies and rules according to different management rules
- Assigning the end equipment to designated VLAN based on the identity of the user
- Supporting the management with switches of different vendors
- Using unified management interface to simplify IT work
- Identifying and monitoring the connected devices in the company and their status instantly
- Creating audit logs of the company intranet
To prevent data breach disguised as legitimate actions, OUCC uses a Privilege Access Management (PAM) system to avoid credential theft and the threats caused by privilege abuse.
To manage the user accounts of the system, the random one-time passwords are generated, and become invalid upon the completion of each task to prevent or reduce the risk of lost or hacked passwords.
With Green IT as the ESG ultimate goal to net-zero emission, the Data Center Cloudification Project in 2023 was scheduled as follows:
- Only network equipment remained at the IT hubs in Taipei and Kaohsiung.
- All servers in the original IT hubs were transferred to the Cloud.
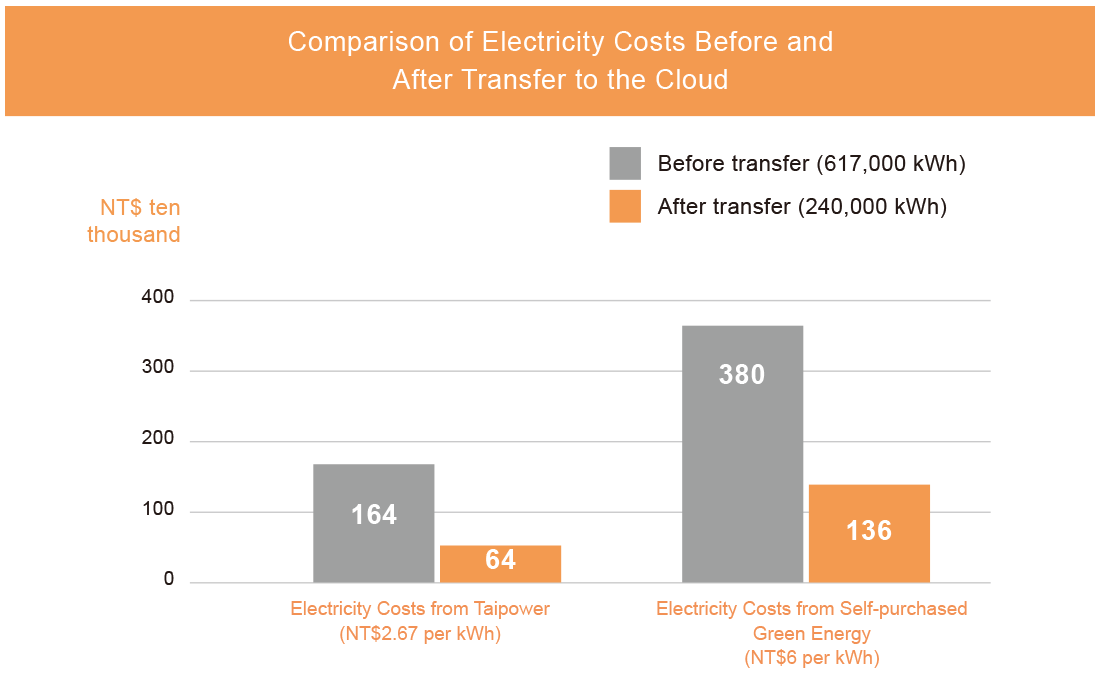
Effects:
- The space of the IT hub could be reused
- Achieve the ESG net-zero emission target
- Resources may be swiftly adjusted at the cloud according to needs
» Cloud service offers the purposes of no equipment procurement, easy expansion or removal by demand, cost effective and quick introduction.
» Cost is charged based on the amount of usage with more flexibility.
Stakeholders Contactors
- Mr. Chen/Ms. Chang
- E-mail: ESG@oucc.com.tw
SHE Contactors
- Mr. Yeh/Mr. Wu
- E-mail: she@oucc.com.tw

